– Dr. Hongwen Zhang, CEO of Wedge Networks (www.wedgenetworks.com), says:
Network traffic in data centers is growing in volume and complexity; traditional network filtering technologies are unable to keep up with malicious malware sneaking onto the network. Currently, one in every 14 downloads are infected with malicious content that may cause reputational and customer relationship management challenges. According to PwC’s 2012 Global State of Information Security Survey, only 43 percent of security experts believe that their information security strategy is adequate. When malicious content and non-compliant data pass through a network undetected, data centers experience setbacks from information leakage and possible IT infrastructure damage.
With the proliferation of mobile data usage, social media and cloud computing, a new portfolio of security threats have emerged, requiring a different approach to advance current security practices. Traditional inspection technologies that secure data center networks at the packet level, such as packet filtering and Deep Packet Inspection (DPI), have limited efficiency and are unable to scale to provide clean and safe usage of the evolving Internet.
Out With the Old: Deep Packet Inspection
Today, Deep Packet Inspection is the most widely adopted solution for monitoring and managing network packet data. DPI matches the IP packet sequences against a library of offending patterns. To be successful, DPI systems must match the packet information to patterns at wire speed, posing two main limitations:
· Malware that is often embedded in large application payloads may slip through a system undetected. This is because a DPI system is only capable of holding a limited amount of packets at a time for pattern matching. The amount of IP packets required to transmit an application payload often surpass the number of packets that a DPI system can inspect at any given moment, creating a hole for malware to slip onto the network.
· A DPI system obtains packet data and matches it against known malware threats, however the number of unique signatures available for the system to match against is restricted.
Data centers fail to achieve optimal network security as a result of the limitations of DPI. The growing number of unsupported application types with nested, zipped or archived files, exploit DPI limitations and can slip through security systems that are not qualified to handle them.
In With the New: Deep Content Inspection
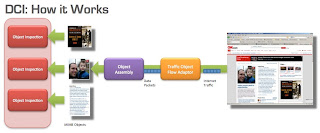
A new approach to data inspection is needed that incorporates thorough analysis to address the undetected and emerging threats, Deep Content Inspection (DCI) is an advanced form of network filtering that functions as a fully transparent device at a comprehensive level. DCI examines the entire object and detects any malicious or non-compliant intent, instead of solely checking the body or header of data packets circling through a network. DCI reconstructs, decompresses and/or decodes network traffic packets into their constituting application level objects, often referred to as the MIME objects.
The predominant DCI standard implements full content-based review in real time to understand the intent of data-in-motion. This method transcends the DPI approach of simply matching packet sequences against known patterns and allows DCI to gain a wider inspection scope. This new method of network inspection offers an increased level of security by performing reputation searches and behaviour analyses on structured or packed data. DCI finds and assesses signatures that cross packet boundaries by keeping track of content across multiple packets.
By transitioning away from traditional packet inspection and concentrating on the content and intent of data, DCI provides a comprehensive method of filtering for attacks and malicious content. This approach secures data centers, enterprises, government organizations, service providers and carrier networks against today’s evolving threats.
About the Author:
Dr. Hongwen Zhang is president and CEO of Wedge Networks, a leading provider of remediation-based Deep Content Inspection for high-performance, network-based Web security. He holds a PhD in Computer Science from the University of Calgary; a MSc in Computer Engineering from the Institute of Computer Technology – Chinese Academy of Sciences (Beijing, PRC), and a Bachelor of Science in Computer Science from Fudan University (Shanghai, PRC). With more than two decades of high tech leadership experience, Dr. Zhang is a co-inventor and holder of several patents in the area of computing and networking.