By Gary Kinghorn, Director of Product Marketing, Forward Networks
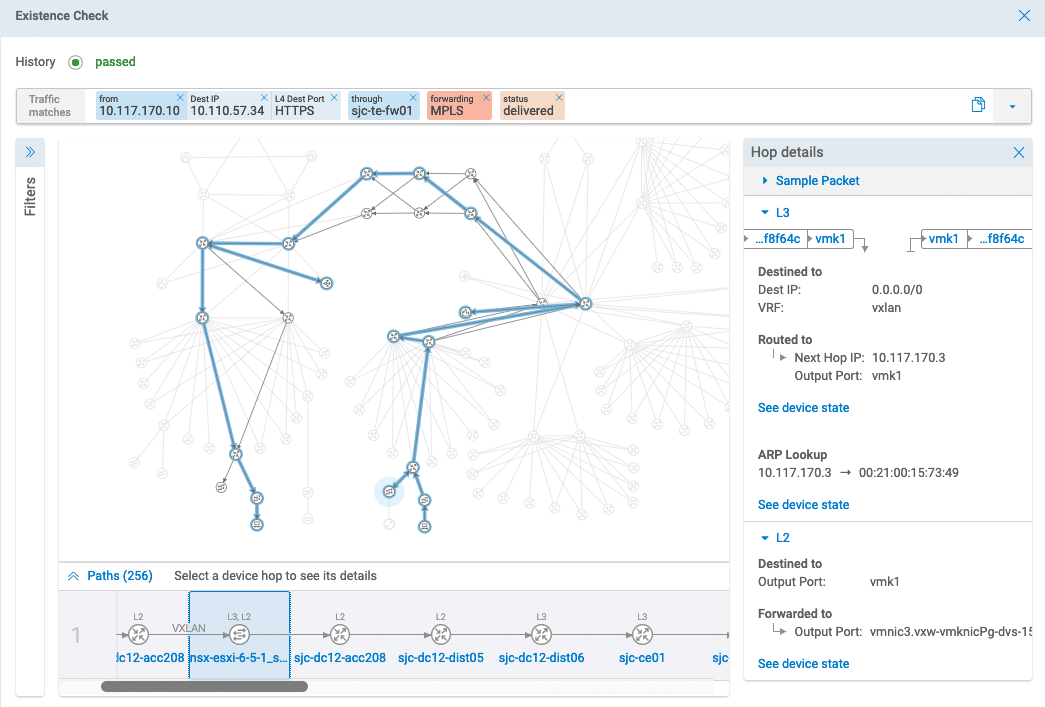
The challenge with IBN systems is to codify network intelligence and analytical capabilities into a general-purpose platform for all traffic, devices and protocols. The problem becomes much easier and more realistic when the focus is narrowed to verifying that the existing network design is in alignment with intended policies. Intent-based verification thus compares a series of high-level policy statements and requirements to verify that the network is correctly designed and configured to support them, and suggesting changes where needed.
Verifying network designs and configurations can be tedious, time intensive and expensive, making the process an excellent candidate for IT automation where possible. Since IT teams are now focused heavily on digital transformation and IT automation, the question naturally arises how intent-based verification can support these efforts. Three primary areas are commonly addressed by data center organizations:
- Root cause analysis and accelerating trouble ticket resolution
- Compliance and audit-related processes
- Change window validation
Root-Cause Analysis and Remediation of Network Issues
When network issues arise unexpectedly, isolating the root-cause is often a challenge. For example, users and network admins can observe that a certain type of traffic flow between source and destination is down, but the specific device configurations or firewall rules that determine the current behavior are hard to isolate. Seemingly unrelated changes may have adverse impact to application flows and users in another part of the network.
IBN systems can automate much of the root-cause analysis around high-level traffic flows, or what is intended to happen. A detailed analysis of the entire network that can quickly isolate what is preventing a particular flow or behavior can now be completed in a few minutes. The innovation from IBN allows search queries and analysis on end-to-end traffic flows, which map to high-level requirements and have intelligence baked into the system to analyze the low-level device details and isolate what changes need to be made.
IBN deployments are now seeing around 25-50 percent reduction in time and resources to resolve trouble tickets caused by configuration errors or unexpected changes in the operational state of network devices. In the case of large enterprise networks this can translate to thousands of hours per year.
Compliance and Audit-Related Tasks
Most compliance checks and network audits require verifying key aspects of network behavior, making them prime candidates for process automation through IBN. IBN platforms can verify security policies, such as confirming specific subnets and tenants are isolated, or that all external application access is through S-HTTP only. Fault-tolerance and path, or device, redundancy can also be quickly verified at a glance, with automated checks running each hour or each day, as needed.
IBN systems can also automate the search and remediation for a wide range of audit-related network health checks, which are difficult to find manually, such as:
- Link speed mismatches
- Maximum Transmission Unit (MTU) size mismatches
- Forwarding loops
- VLAN definition inconsistencies
- Port channel inconsistencies
Compliance objectives are a natural fit for IBN verification where policy requirements can be specified. Audit-related processes can likely complete in a fraction of the time. To the extent that an IBN system can archive network snapshots and audit reports, organizations can easily track compliance results over time and compare to then-current differences in network design. This can give IT organizations a powerful tool to document, track and report on network behavior changes over time for the first time.
Change Window Validation and Post-Change Verification
Perhaps the most important times to verify network behavior and capabilities are both before and after a change window. Roughly one-third of all change windows fail because of faulty change procedures, unexpected network conditions, limited test ability or user error. Verifying all network capabilities in both scenarios will immediately expose if there is any adverse or unintended impact from a set of changes or upgrades. Because changes always introduce risk into a running network, and unforeseen issues post-deployment frequently require roll-backs, verifying changes prior to deployment can reduce these concerns measurably, as well as the time to get the changes deployed.
Increasingly, large data center network updates are being rolled out by or in conjunction with automation and orchestration platforms. IBN verification solutions are now being deployed with these orchestration platforms to ensure that all processes are automated, and that they are implemented correctly with minimal human intervention. Common automation tools that could benefit from network verification technology include Ansible, Cisco Network Services Orchestrator (NSO), Cisco ACI, NFV orchestration, OpenStack, or container-based orchestration such as Kubernetes.
Summary
Intent-based verification can now deliver a revolutionary approach to analyzing and troubleshooting complex network issues, as well as allowing functional validation of network designs and changes. Cost savings from leveraging emerging IBN verification solutions can be a significant percentage of network IT costs when factored over the areas of trouble ticket resolution, audit-related fixes and reducing the time spent in change windows. Based on these process improvements and savings, we expect intent-based verification to be an important part of IT networking strategy going forward and future network automation projects.
About the Author:




